Today, in a certain group of experts, a group member shared a miraculous disk that has increased nearly 100 times in less than 24 hours.
https://dexscreener.com/ethereum/0xd809d08876f7c45c0a760f2066f838ddfef91b61
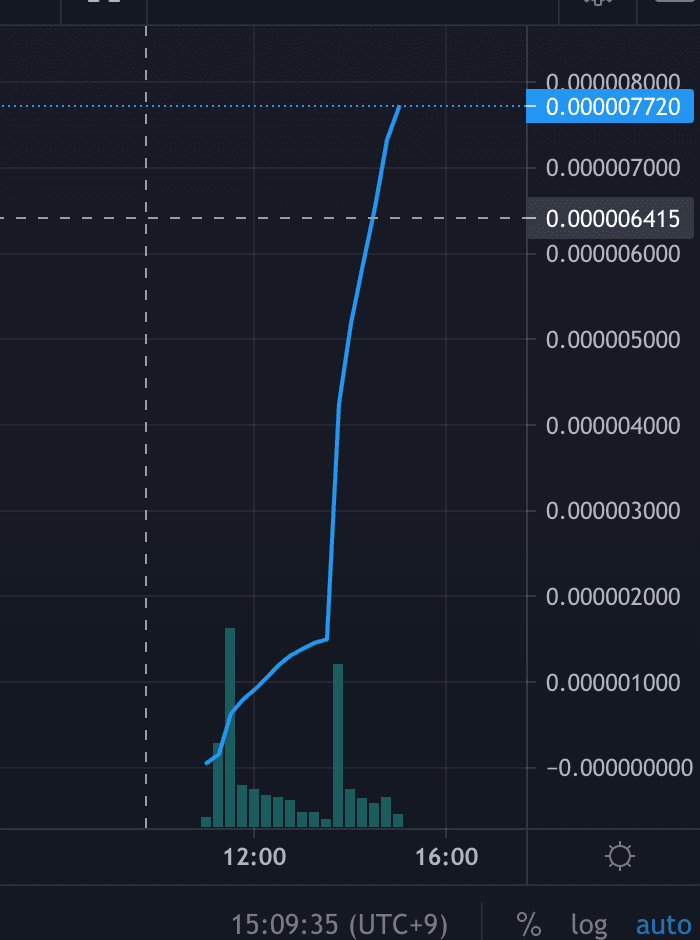
Several group members eagerly rushed in. After a while, they found that it had actually doubled and were very happy. So they wanted to sell it first, but found that they couldn't sell it?
However, all the checks on the market show that this is not a honeypot. For example, the report from tokensniffer:
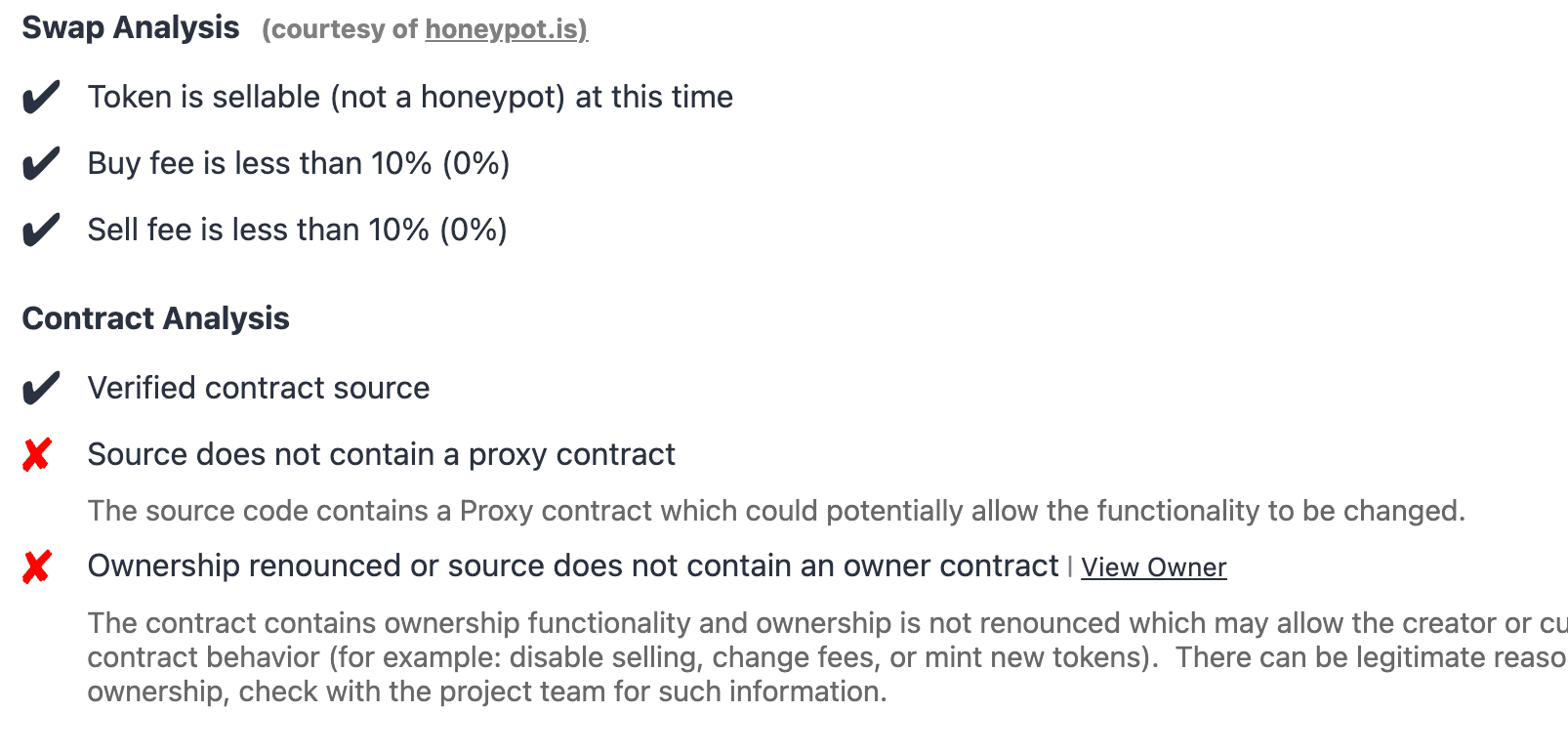
So what's the reason for this?
The key point lies in this sentence: Source does not contain a proxy contract
As mentioned in my own message in the screenshot above, this contract
0xd809d08876f7c45c0a760f2066f838ddfef91b61
is not a real ERC20 contract, it is just a proxy. All the real interactions are in the logic contract. The purpose of the proxy contract is just to call the logic contract to do things.
https://tokensniffer.com/contract/0x39ff02669ad11fd46674150cbfca6b46b4e4b908
Here we can see the source code of the contract. It is obvious that it uses EIP-1967. If you have played the squid game, you should be familiar with this honeypot.
EIP-1967 defines a universal storage slot for storing the address of the logic contract in the proxy contract at a specific location. If you don't understand the above sentence, it doesn't matter. In simple terms, using EIP-1967, there is a place in the contract that can be used to store the address of the real contract (referred to as the "logic contract" mentioned above). And all the real interactions are in the real contract.
We can construct the logic contract address through the constructor:
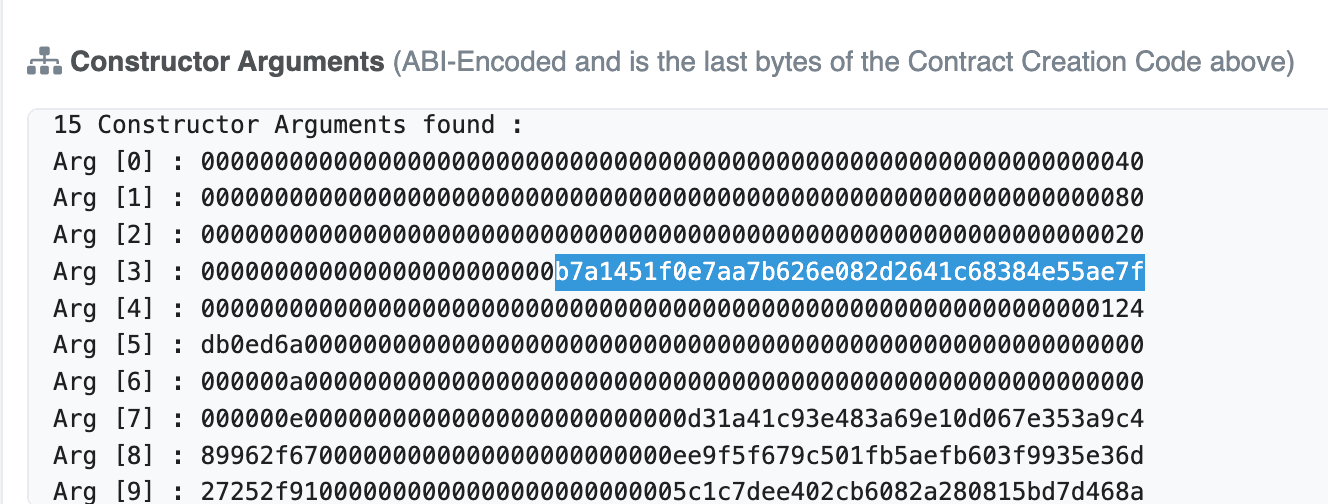
https://etherscan.io/address/0xb7a1451f0e7aa7b626e082d2641c68384e55ae7f
Unfortunately, it is not open source.
Therefore, it is completely impossible to detect the logic contract when detecting the proxy contract.
Let's talk about those accounts that can sell. As you can see from the analysis above, the real contract should have a whitelist logic that allows only addresses in the whitelist to sell tokens. And all these accounts that can sell are owned by the scammer himself.
For example, let's randomly select a transaction for selling:
https://etherscan.io/tx/0x0a16b0119386c7ebe072051090f1478c8aacae1ae8add4ed0f88cebc2a9f7f85
It can be seen that this address
0x13729552cd898c823abeb0eddd8714f4642688ee
https://etherscan.io/address/0x13729552cd898c823abeb0eddd8714f4642688ee
has only three transactions, one of which transferred an ETH (probably for fees), and the other two were for selling. Huh? Why is there no record of buying tokens at all? How did this person get the tokens to sell? Actually, it's simple. Adding tokens doesn't necessarily require a purchase. As long as the real contract has this code:
accounts[address] = accounts[address].add(amount); // Add the amount of tokens to any address (address)
It is possible to add tokens to any address without the need for token distribution or self-purchase through transactions.
Let's dig deeper into where the 1 ETH that was transferred in came from.
Due to the large number of layers involved, some irrelevant accounts have been omitted in the middle, and we finally arrived at this address:
0xae155cb9857bf0870d6965ead4482552fbb12f32
https://etherscan.io/address/0xae155cb9857bf0870d6965ead4482552fbb12f32
It can be seen that this address is identical to the previous one, 0x13729552cd898c823abeb0eddd8714f4642688ee. It received a certain amount of ETH and sold non-existent tokens to obtain ETH—except this time, the tokens are not called paramount, but a token called ULV (Uniswap Labs Ventures).
https://etherscan.io/token/0x90d33aff810f15ac0e5247e7b93c1f225cb1b884
This ULV is also a honeypot, just like paramount. We can see that a part of the ETH transferred out by 0xae155cb9857bf0870d6965ead4482552fbb12f32 went to this address:
0x2de4b6dbd147e773ff054bdfb96f0081ecce9617
And what is this address for?
It's simple, it's used to pump ULV.
https://etherscan.io/tx/0xf4be294b9e794b0655b97a5d2e48e0dadd000af88980dbc6c5a56723bc7c4db8
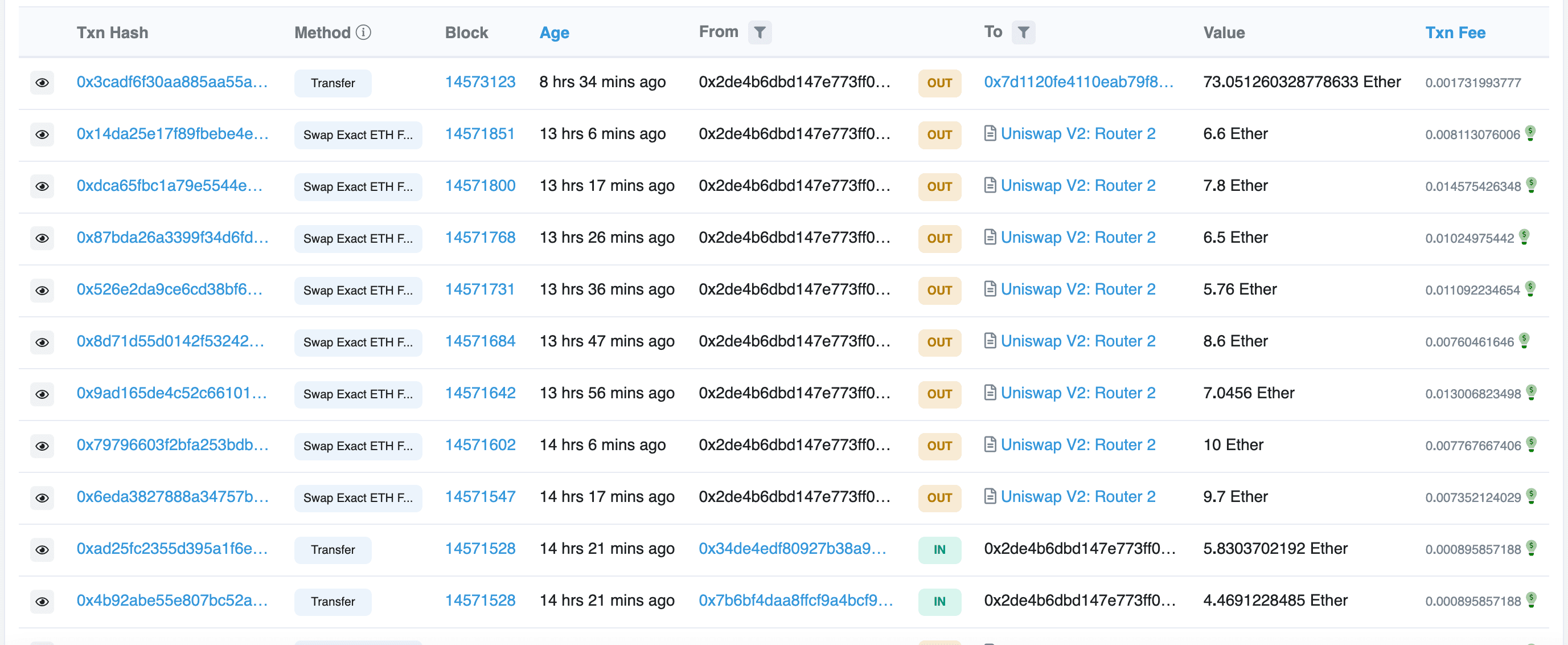
It can be seen that half of the large purchases of ULV are made by this address (there are also several addresses assisting in pumping). Finally, 73 ETH is transferred out as profit.
And the address that received 73 ETH, 0x7d1120fe4110eab79f854a4ab7895d44a7a5f58d, is another pumping address for a token called UIP (United International Pictures).
https://etherscan.io/address/0x7d1120fe4110eab79f854a4ab7895d44a7a5f58d
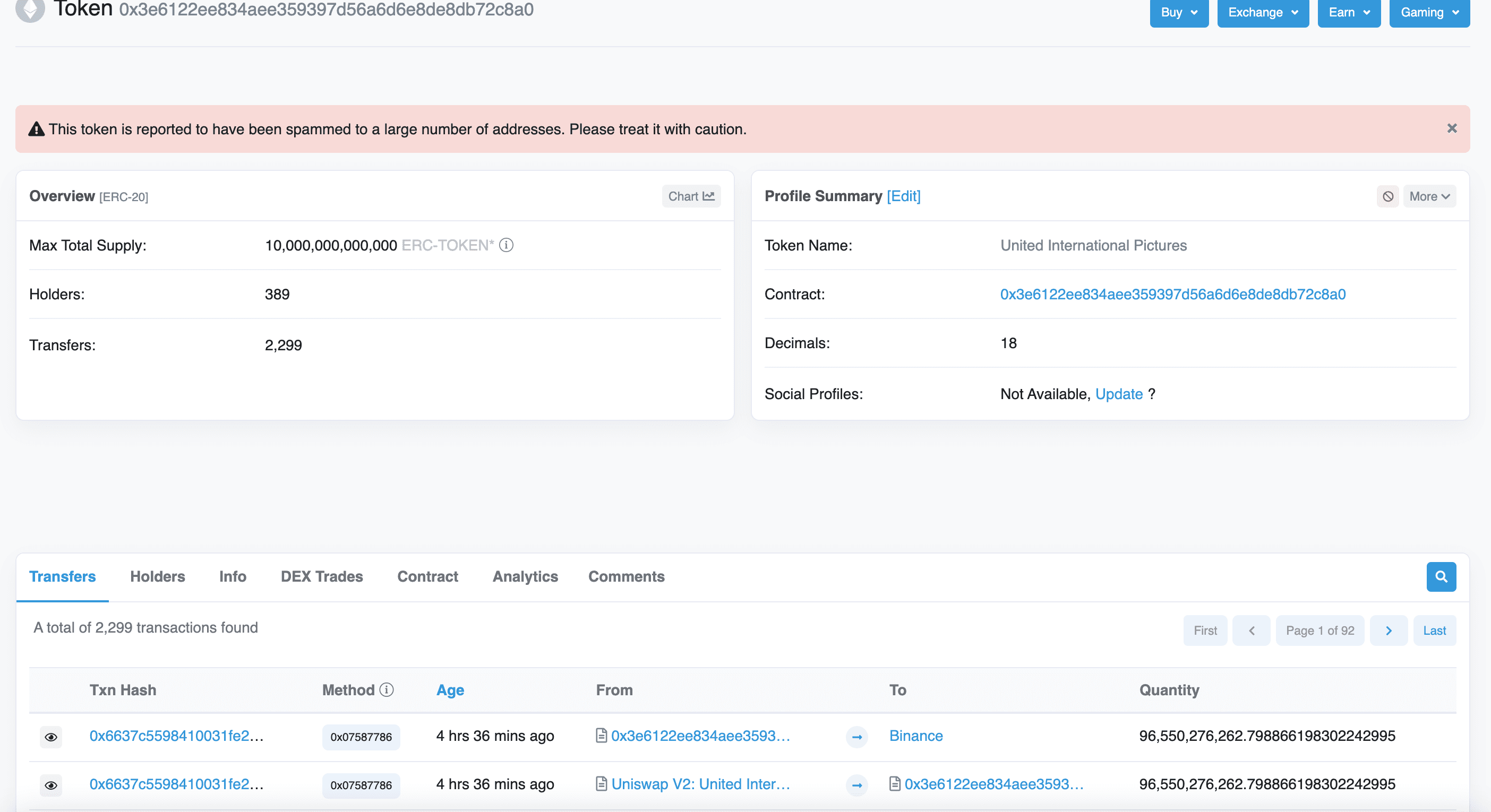
Therefore, the whole chain is clear: deploy a proxy contract, create an air coin → add addresses that can sell to the real contract whitelist in advance → add tokens to these addresses → airdrop to well-known addresses → attract people to buy, and the addresses that can sell sell for profit → a portion of the funds are transferred to pumping addresses to continuously pump → finally exit and switch to the next honeypot
Except for the scammer himself, no one else can sell, and the scammer himself keeps buying with a portion of the ETH, so the price of the token keeps skyrocketing.
P.S: By the way, this team really likes to use brand names from the real world as token names. Some of the names we have discovered include Hilton, Panasonic, Hitachi, and so on.
Follow me to get more blockchain technology news: